AWS: Connecting to Your Linux Instance from Windows Using PuTTY
After you launch your instance, you can connect to it and
use it the way that you'd use a computer sitting in front of you.
Note
After you launch an instance, it can take a few minutes
for the instance to be ready so that you can connect to it. Check that your
instance has passed its status checks - you can view this information in the Status Checks column on the Instances page.
The following instructions explain how to connect to your
instance using PuTTY, a free SSH client for Windows. If you receive an error
while attempting to connect to your instance, see Troubleshooting Connecting to
Your Instance.
Prerequisites:
Before you connect to your Linux instance using PuTTY,
complete the following prerequisites:
Install PuTTY
Download and install PuTTY from the PuTTY download page.
Be sure to install the entire suite.
Get the ID of the
instance
You can get the ID of your instance using the Amazon EC2
console (from the Instance ID column). If you prefer, you can use the
describe-instances (AWS CLI) or ec2-describe-instances (Amazon EC2 CLI)
command.
Get the public DNS
name of the instance
You can get the public DNS for your instance using the
Amazon EC2 console (check the Public DNS column; if this column is hidden,
click the Show/Hide icon and select Public DNS). If you prefer, you can use the
describe-instances (AWS CLI) or ec2-describe-instances (Amazon EC2 CLI)
command.
Locate the private
key
You'll need the fully-qualified path of the .pem file for
the key pair that you specified when you launched the instance.
Enable inbound SSH
traffic from your IP address to your instance
Ensure that the security group associated with your
instance allows incoming SSH traffic from your IP address. For more information,
see Authorizing Network Access to Your Instances.
Important: Your
default security group does not allow incoming SSH traffic by default.
Converting Your
Private Key Using PuTTYgen
PuTTY does not natively support the private key format
(.pem) generated by Amazon EC2. PuTTY has a tool named PuTTYgen, which can
convert keys to the required PuTTY format (.ppk). You must convert your private
key into this format (.ppk) before attempting to connect to your instance using
PuTTY.
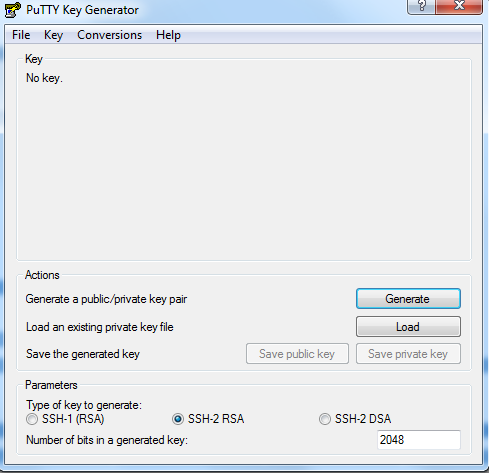
To convert your
private key
1. Start PuTTYgen (for example, from the Start menu,
click All Programs > PuTTY > PuTTYgen).
2. Under Type of key to generate, select SSH-2 RSA.
3. Click Load. By default, PuTTYgen displays only files
with the extension .ppk. To locate your .pem file, select the option to display
files of all types.
4. Select your .pem file for the key pair that you
specified when you launch your instance, and then click Open. Click OK to
dismiss the confirmation dialog box.
5. Click Save private key to save the key in the format
that PuTTY can use. PuTTYgen displays a warning about saving the key without a
passphrase. Click Yes.
Note
A passphrase on a private key is an extra layer of
protection, so even if your private key is discovered, it can't be used without
the passphrase. The downside to using a passphrase is that it makes automation
harder because human intervention is needed to log on to an instance, or copy
files to an instance.
6. Specify the same name for the key that you used for
the key pair (for example, my-key-pair). PuTTY automatically adds the .ppk file
extension.
Your private key is now in the correct format for use
with PuTTY. You can now connect to your instance using PuTTY's SSH client.
Starting a PuTTY
Session
Use the following procedure to connect to your Linux
instance using PuTTY. You'll need the .ppk file that you created for your
private key. If you receive an error while attempting to connect to your
instance, see Troubleshooting Connecting to Your Instance.
To start a PuTTY
session
1. (Optional) You can verify the RSA key fingerprint on
your instance by using one of the following commands on your local system (not
on the instance). This is useful if you've launched your instance from a public
AMI from a third party. Locate the SSH HOST KEY FINGERPRINTS section, and note
the RSA fingerprint (for example,
1f:51:ae:28:bf:89:e9:d8:1f:25:5d:37:2d:7d:b8:ca:9f:f5:f1:6f) and compare it to
the fingerprint of the instance.
get-console-output
(AWS CLI)
aws
ec2 get-console-output --instance-id instance_id
ec2-get-console-output
(Amazon EC2 CLI)
ec2-get-console-output
instance_id
Note
The SSH HOST KEY FINGERPRINTS section is only available
after the first boot of the instance.
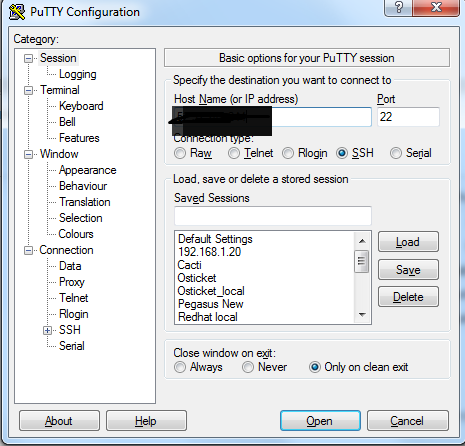
2. Start PuTTY (from the Start menu, click All Programs
> PuTTY > PuTTY).
3. In the Category pane, select Session and complete the
following fields:
a) In the Host Name box, enter user_name@public_dns_name.
Be sure to specify the appropriate user name for your AMI. For example:
- For an Amazon Linux AMI, the user name is ec2-user.
- For a RHEL5 AMI, the user name is either root or ec2-user.
- For an Ubuntu AMI, the user name is ubuntu.
- For a Fedora AMI, the user name is either fedora or ec2-user.
- For SUSE Linux, the user name is either root or ec2-user.
- Otherwise, if ec2-user and root don't work, check with the AMI provider.
b) Under Connection type, select SSH.
c) Ensure that Port is 22.
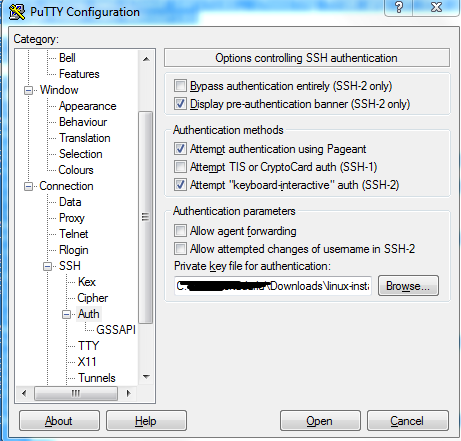
4. In the Category pane, expand Connection, expand SSH,
and then select Auth. Complete the following:
Click Browse.
Select the .ppk file that you generated for your key
pair, and then click Open.
(Optional) If you plan to start this session again later,
you can save the session information for future use. Select Session in the
Category tree, enter a name for the session in Saved Sessions, and then click
Save.
Click Open to start the PuTTY session.
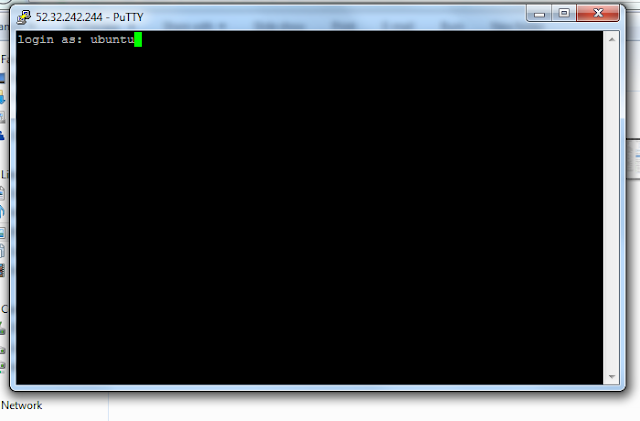
5. If this is the first time you have connected to this
instance, PuTTY displays a security alert dialog box that asks whether you
trust the host you are connecting to.
6. (Optional) Verify that the fingerprint in the security
alert matches the fingerprint that you obtained in step 1. If these
fingerprints don't match, someone might be attempting a
"man-in-the-middle" attack. If they match, continue to the next step.
7. Click Yes. A window opens and you are connected to
your instance.
Note
If you specified a passphrase when you converted your
private key to PuTTY's format, you must provide that passphrase when you log in
to the instance.
Keywords: Putty, AWS Linux Instance, Putty keygen, AWS Ubuntu Instance


Comments
Post a Comment